Actions
Bug #3333
closedUpdate LibreSSL to 3.6.1
Added by tuxillo about 3 years ago. Updated about 3 years ago.
Description
We're currently using LibreSSL 3.2.5 in base, which is quite old. Need to upgrade to the latest stable, which at the moment is 3.6.1
Following tests are required:
- Test encrypted root installation and boot
- Test pkgng
- Test openssl
- Test ldns consumers
- Test usr.bin/dc
- Test usr.bin/nc
Files
| encrypted_root_361.png (29 KB) encrypted_root_361.png | tuxillo, 11/25/2022 12:29 PM | ||
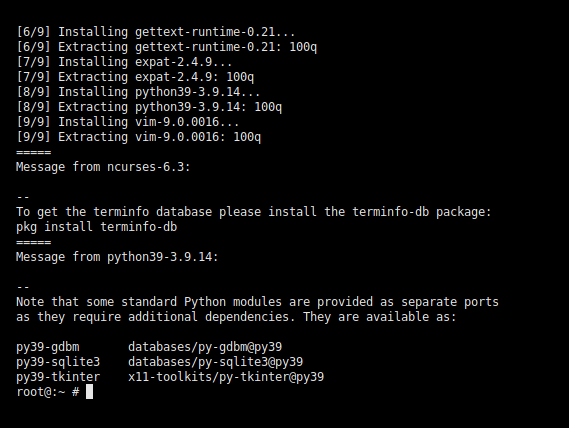
| install-vim-from-avalon.png (27.9 KB) install-vim-from-avalon.png | tuxillo, 11/25/2022 01:21 PM |
 Updated by tuxillo about 3 years ago
Updated by tuxillo about 3 years ago
- Description updated (diff)
- Status changed from New to In Progress
 Updated by tuxillo about 3 years ago
Updated by tuxillo about 3 years ago
- File encrypted_root_361.png encrypted_root_361.png added
 Updated by tuxillo about 3 years ago
Updated by tuxillo about 3 years ago
 Updated by tuxillo about 3 years ago
Updated by tuxillo about 3 years ago
Test openssl¶
root@:~ # openssl version LibreSSL 3.6.1 root@:~ # echo | openssl s_client -connect google.com:443 | openssl x509 -issuer -noout depth=2 C = US, O = Google Trust Services LLC, CN = GTS Root R1 verify return:1 depth=1 C = US, O = Google Trust Services LLC, CN = GTS CA 1C3 verify return:1 depth=0 CN = *.google.com verify return:1 issuer= /C=US/O=Google Trust Services LLC/CN=GTS CA 1C3 DONE root@:~ # openssl speed sha256 Doing sha256 for 3s on 16 size blocks: 12803356 sha256's in 3.02s Doing sha256 for 3s on 64 size blocks: 6832362 sha256's in 3.02s Doing sha256 for 3s on 256 size blocks: 3006491 sha256's in 3.02s Doing sha256 for 3s on 1024 size blocks: 911102 sha256's in 3.02s Doing sha256 for 3s on 8192 size blocks: 111166 sha256's in 3.02s LibreSSL 3.6.1 built on: date not available options:bn(64,64) rc4(16x,int) des(idx,cisc,16,int) aes(partial) idea(int) blowfish(idx) compiler: information not available The 'numbers' are in 1000s of bytes per second processed. type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes sha256 67793.60k 144878.18k 254571.21k 309190.00k 301323.08k root@:~ # openssl req -nodes -new -x509 -keyout server.key -out server.cert Generating a 2048 bit RSA private key ................................ ............................. writing new private key to 'server.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) []:US State or Province Name (full name) []:California Locality Name (eg, city) []:None Organization Name (eg, company) []:Here Organizational Unit Name (eg, section) []:OU Common Name (eg, fully qualified host name) []:mytest.test.com Email Address []: root@:~ # openssl x509 -in server.cert -noout -subject -issuer subject= /C=US/ST=California/L=None/O=Here/OU=OU/CN=mytest.test.com issuer= /C=US/ST=California/L=None/O=Here/OU=OU/CN=mytest.test.com
 Updated by tuxillo about 3 years ago
Updated by tuxillo about 3 years ago
Test ldns consumers¶
root@:~ # drill -TD google.com Warning: No trusted keys were given. Will not be able to verify authenticity! ;; Domain: . ;; Signature ok but no chain to a trusted key or ds record [S] . 172800 IN DNSKEY 256 3 8 ;{id = 18733 (zsk), size = 2048b} . 172800 IN DNSKEY 257 3 8 ;{id = 20326 (ksk), size = 2048b} Checking if signing key is trusted: New key: . 172800 IN DNSKEY 256 3 8 AwEAAeB54o2xvW6vY4qQZ0krDsEZCe6MsRWCqsXd4+cNJZMePnlV/xwDrIbbeH1SJzv742rOHzgAKM1/3SQHHSkoEIPx8XQdHAZBxfhaXl3e8c5WrE3aGXS5AeTWAkt85ccqWgKyitxjFmJEOol0BqS2xueltaDwgWcC10nPUY+y5l/kTOYyptYQS4gg1uJNXIob/R1XIEJ10ZCurkYqZxgqyHc7tZv09N23o9rnGdjnYiArH7FjlXD8Rvjde8YWkmfdbCEWnchrnxDK8KV2/ZvBpG/WYnRKXYPUceGCw59OJdJ5M7utkm547RB3eEd8CVVhbXopZlsKq3GCrBwaIVe9ci0= ;{id = 18733 (zsk), size = 2048b} [S] com. 86400 IN DS 30909 8 2 e2d3c916f6deeac73294e8268fb5885044a833fc5459588f4a9184cfc41a5766 ;; Domain: com. ;; Signature ok but no chain to a trusted key or ds record [S] com. 86400 IN DNSKEY 256 3 8 ;{id = 53929 (zsk), size = 1280b} com. 86400 IN DNSKEY 257 3 8 ;{id = 30909 (ksk), size = 2048b} [S] Existence denied: google.com. DS ;; No ds record for delegation ;; Domain: google.com. ;; No DNSKEY record found for google.com. [U] google.com. 300 IN A 172.217.17.14 ;;[S] self sig OK; [B] bogus; [T] trusted; [U] unsigned
 Updated by tuxillo about 3 years ago
Updated by tuxillo about 3 years ago
Test usr.bin/dc
h3. Test usr.bin/nc¶
root@:~ # dc [la1+dsa*pla10>y]sy 0sa1 lyx 1 2 6 24 120 720 5040 40320 362880 3628800 root@:~ # nc -cv -T protocols=all www.google.es 443 Connection to www.google.es (142.250.185.3) 443 port [tcp/https] succeeded! TLS handshake negotiated TLSv1.3/TLS_AES_256_GCM_SHA384 with host www.google.es Peer name: www.google.es Subject: /CN=*.google.es Issuer: /C=US/O=Google Trust Services LLC/CN=GTS CA 1C3 Valid From: Wed Nov 2 13:46:42 2022 Valid Until: Wed Jan 25 13:46:41 2023 Cert Hash: SHA256:6ff244af5060ca6ec4c1a0c9acf209ea5c0ccf2915b260de41b2e008217c5d7f OCSP URL: http://ocsp.pki.goog/gts1c3
Actions